When I first started using Linux, I often got confused about the concept about users, groups, permissions and other kind of stuff. Therefore like all beginners, I tried to stick to the root user just to avoid typing sudo(as I did not understand why I had to use it) and this turned out to be a great mistake.
In this tutorial, I will guide you on how Linux users and permissions work, how to manage them and more importantly, Avoid working in the root account unless you have to!
Users and Groups Permissions
Like most operating System, Linux supports the functionality of multitasking. However, unlike others, Linux allows more than one user to have access to the system in a single instance. Therefore to ensure that users do not interfere and manage files and directories from other users a method of protection is implemented. This protection mechanism is known as linux permissions.
Linux Permissions - Read, Write and Execute
In simple terms, permissions are simply permit or approval to perform actions on a file or a directory. For example the permission to read allows the user or users of that group to view the contents of the file.
The three basic rights are read, write and execute.
read- The read permission allows the contents of the file to be viewed by the respective users or groups. On a directory, thereadpermission allows you to view the files and sub-directories within it.write- Write permissions allows users to perform modifications to the files and directories. For example, you can edit the contents of areadme.txtfile ordelete,createfiles and directories within other directories.Execute- The execute permission as the name suggest allows users to run the file or execute a script or a program.Executepermission on a directory allows users and groups to change to different directory and use it as the working directory.
In most cases, users are members of a single group but can be members of more than one groups available in the system.
Listing File and Directory Permissions
You can view the permissions of a file or directory within the filesystem using the command ls -la [FILE, DIRECTORY].
The contents within the square brackets [] are replaced with the name of the file or directory. If the file or directory is not within the current working directory, you will have to pass the full path of the files.
For example, let us create a file in the Desktop and view its permissions:
cd /home/user/Desktop # navigate to the desktop
touch permissions.txt # create a new file
cd # change back to the home directory
ls -la /home/user/Desktop/permissions.txt # provide the full path of the fileThe above commands should give an output as shown below- I know the commands above are unnecessarily long but it illustrates navigating directories and file paths - three birds in one stone.
-rw-rw-rw- 1 csalem csalem 0 Jun 12 03:27 /home/csalem/Desktop/permissions.txtAs you can see, the first ten characters, including the dashes shows the permissions set on the file. The first dash (-) shows what type of file where - represents a regular file, a d represents a directory and finally an s which represents a special file.
The next three characters rw- are used to define the owner’s permissions on that file or directory. From the example above, we see the user has read and write permissions to that file.
The following 3 characters rw- represents the permissions for members of the same group as the owner of the file. In the above examples, members of same group can read and write.
Finally, the last three characters rw- shows the permissions for all other users. As shown in the example, read and write permissions are allowed.
We will cover how to set permissions in the next sections.
Managing Users and Groups
In this section, we are going to cover how to manage users and groups showing you how to create, delete and modify users and groups in a Linux system. Some commands may require you to use sudo. Ironically we cover sudo user in this tutorial.
Creating users
To create a new user account in Linux, we use the useradd command. The general syntax is:
useradd [username] By default, the username should be unique across the system. The useradd command also accepts arguments to control the functionality of the command. The most common arguments include:
| Argument | Functionality | Example |
|---|---|---|
-d <HOME_DIR> |
specifies the user’s login directory | useradd [username] /home/myusername |
-m <HOME> |
creates user’s home directory. | useradd [username] -m /home/myusername |
-s <SHELL> |
specifies the default shell type for the user | useradd [username] -s /bin/zsh |
-e <DATE> |
sets the date which the account is set to expire | useradd [username] -e <YYYY-MM-DD> |
-f <INACTIVE> |
sets the number of days before the account expires | useradd [username] -f <0 or -1> |
-u <UID> |
sets the ID of the new account | useradd [username] -u <non-negative int value> |
There are other options that are acceptable by the useradd command. Check the manual pages with the command.
man useraddhttps://www.man7.org/linux/man-pages/man8/useradd.8.html
Once a user is created, you will require to set a password using the passwd <username> command. This command is also used to change the password for the specified user.
sudo passwd myusername
New password:
Retype new password:
passwd: password updated successfullyUse sudo when creating accounts to avoid permission denied errors!. Example:
useradd myusername
useradd: Permission denied.
useradd: cannot lock /etc/passwd; try again later.There is an easier way to create user account using the adduser command. However, this may require you to install the adduserpackages. You can install it using the command - Debian Based distributions.
sudo apt-get adduser -yOnce installed, you can use the command to automate the process of user creation.
To create a standard user with the adduser command, the syntax is
sudo adduser <username>This will provide a series of prompts to provide details about the user. Most of the information is optional However, a username should be provided.
$ sudo adduser newuser
Adding user `newuser' ...
Adding new group `newuser' (1002) ...
Adding new user `newuser' (1002) with group `newuser' ...
Creating home directory `/home/newuser' ...
Copying files from `/etc/skel' ...
New password:
Retype new password:
passwd: password updated successfully
Changing the user information for newuser
Enter the new value, or press ENTER for the default
Full Name []: New User
Room Number []: 445
Work Phone []: 866-111-212
Home Phone []: 854-989-003
Other []:
Is the information correct? [Y/n] YYou should provide a usernanme matching the set regular expressions under NAME_REGEX[_SYSTEM] variable. You can use --force-badname to forcefully use a username not matching the regex.
For security reasons, ensure to provide strong and unique passwords. I don’t have to say it but just in case DO NOT SHARE PASSWORDS WITH OTHER USERS
Deleting users
To remove a user from the system, you simply enter the command userdel followed by their username.
If no other options are passed to the command, only the user account is removed while files and directories related to the user are retained.
Available options include:
| Argument | Functionality | Example |
|---|---|---|
-f --force |
Forcefully removes the file even if not owned by the specified user | userdel -f myusername |
-r --remove |
Removes the user’s home directory and mail pool | userdel -r myusername |
-Z --selinux-user |
remove any SELinux user mapping for the user - Requires SELinux enabled Kernel | userdel -r -Z myusername |
Working with groups
One of the ways Linux is able to organize users in a system is use of groups. Groups are mainly a collection of user accounts which are administered using the /etc/group file.
You can view the groups and the members available by viewing the file contents.
sudo cat /etc/group
root:x:0:
daemon:x:1:
bin:x:2:
sys:x:3:
adm:x:4:syslog,csalem
tty:x:5:
disk:x:6:
lp:x:7:
mail:x:8:
news:x:9:
uucp:x:10:
man:x:12:
proxy:x:13:
kmem:x:15:
dialout:x:20:csalem
fax:x:21:
voice:x:22:
cdrom:x:24:csalem
floppy:x:25:csalem
tape:x:26:
sudo:x:27:csalem
audio:x:29:csalem
---OUTPUT TRUNCATED---
csalem:x:1000:
myusername:x:1001:
newuser:x:1002:Each user has a default or primary group. Once a user logins in, the group membership is set for their primary group. This allows Linux to associate files and running programs started by the user with the user’s group. The user may access files and directories in other groups provided they are members of those groups and access permissions are set.
To run create files in different group, the user uses the newgrp command to switch to the current group. For example:
newgrp <admin>If the specified user is a member of the admin group, the current group membership is changed and files created by the user are associated with the current group and the the user’s primary group.
Working With Directories
Although this is basic Linux skills, to create a directory, we use the mkdir command followed by the name of the directory as shown:
mkdir ResourcesYou can add more directory names to create multiple directories at once.
To create a directory and set permissions, use the command:
mkdir -m a=rw ResourcesThe -m option is used to specify the directory mode (chmod) and a=rw set the permissions to all users have read and write permissions on the directory(ies).
The mode of a file is managed using the chmod(change mode) command. The command is used to change permissions on files and directories using either octal number or letters. Letters used to set permissions include:
| Letter | Corresponding Permission |
|---|---|
| r | Read permissions |
| w | Write Permissions |
| x | Execute permissions |
| X | Execute only of file is a directory only |
| s | Set user ID on execution |
| u | Current permissions the file has for owner |
| t | save the program text on swap |
| o | current permission the file has for others not in group |
| g | current permissions files has for users in similar group |
The octal format of the chmod command has to be calculated for each file and directory. As mentioned, the first 10 characters will represent to four digits in octal format. For example, the write permission will correspond to number 2, execute will correspond to number 1 and read will be 4. Thus when calculating octal, you calculate numbers between 0 and 7 for each portion of the permission. The table below shows the octal values.
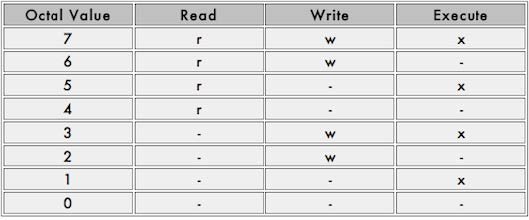
Do not get confused with octal values, they may seem difficult to use but its actually very easy. For example, to set read, write and execute permission using octal values.
sudo chmod 777 Resources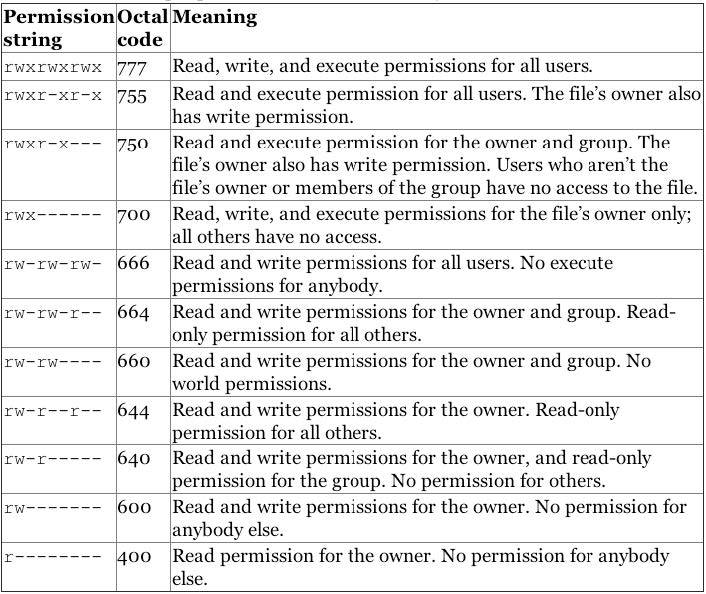
You can view all the mkdir options using the command man mkdir
Remove directories using the rm command. You may need to provide -r for recursive mode. This will remove all the files and sub-directories within the main directory.
rm -rf Resources -vModifying File and Directory Permissions
We discussed how to view the directories and file permissions using the ls -l command. The l flag displays the output in long list while -a shows hidden files and directories (Files and directories that start with a dot(.) )
For example:
cd /
ls -la
total 580
drwxr-xr-x 1 root root 4096 Jun 12 03:18 .
drwxr-xr-x 1 root root 4096 Jun 12 03:18 ..
lrwxrwxrwx 1 root root 7 Apr 23 09:40 bin -> usr/bin
drwxr-xr-x 1 root root 4096 Apr 23 09:49 boot
drwxr-xr-x 1 root root 4096 Jun 13 15:08 dev
drwxr-xr-x 1 root root 4096 Jun 13 15:08 etc
drwxr-xr-x 1 root root 4096 Jun 13 01:32 home
-rwxr-xr-x 1 root root 591344 Jan 1 1970 init
lrwxrwxrwx 1 root root 7 Apr 23 09:40 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Apr 23 09:40 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Apr 23 09:40 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Apr 23 09:40 libx32 -> usr/libx32
drwxr-xr-x 1 root root 4096 Apr 23 09:40 media
drwxr-xr-x 1 root root 4096 Jun 12 03:19 mnt
drwxr-xr-x 1 root root 4096 Apr 23 09:40 opt
dr-xr-xr-x 9 root root 0 Jun 13 15:08 proc
drwx------ 1 root root 4096 Apr 23 09:43 root
drwxr-xr-x 1 root root 4096 Jun 13 15:08 run
lrwxrwxrwx 1 root root 8 Apr 23 09:40 sbin -> usr/sbin
drwxr-xr-x 1 root root 4096 Apr 10 17:57 snap
drwxr-xr-x 1 root root 4096 Apr 23 09:40 srv
dr-xr-xr-x 12 root root 0 Jun 13 15:08 sys
drwxrwxrwt 1 root root 4096 Jun 12 23:14 tmp
drwxr-xr-x 1 root root 4096 Apr 23 09:41 usr
drwxr-xr-x 1 root root 4096 Apr 23 09:43 varThe first column shows the permissions and the type of file. The second column with a single value shows the number of files and directories within the directory. The third column shows the owner and the group followed by the size, date and last time of access. Finally, the name of the directory.
You may note that all directories contain a file size of 4096. In Linux, everything is a file and so is a directory. Therefore, 4096 does not reflect the actual size of the directory just the file that represent the directory.
To set a permission on a directory using letters, use the command chmod +<permission> as shown.
sudo chmod u+r, u+x ResourcesThis adds read and execute permission to the directory “Resources”.
The sudo Account
Linux has a superuser account known as root. This is an administrative account that has permission to do anything including modifying system files. Although some systems have the root user enables by default, it is strongly recommended not to use the root account for regular operations. To add a level of security, the sudo account was introduced to act in place of root account.
The sudo command is used to provide a limited access to another user account and perform various operations in elevated mode. It enables users to use the root administrative permissions without connecting directly to root.
To use sudo, you can install it like any other tool using your distribution’s package manager.
For Debian users.
sudo apt-get install sudo -yHowever, to use the sudo command, the account needs to be a member of the sudo group which is managed by the sudoers file located /etc/sudoers.
You can edit the sudoers file using the visudo command. View the contents of the file using cat.
sudo cat ../sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL:ALL) ALL
# Members of the admin group may gain root privileges
%admin ALL=(ALL) ALL
# Allow members of group sudo to execute any command
%sudo ALL=(ALL:ALL) ALL
# See sudoers(5) for more information on "#include" directives:
#includedir /etc/sudoers.dAfter you have given your user account sudo privileges, save the sudoers file and log out as root. Now log in as your user and test the privileges as your user with sudo access. When a new user needs sudo access, you will now be able to edit the sudoers file with your own login using the sudo visudo command.



